Black Ddesert Knowledge Base Authentication Keys
KBA Alternatives
Discover a better way to establish the identity of your online users with The Identity Verification Solution Buyer's Guide.
Knowledge-Based Authentication (KBA): Promises vs. Reality
![]()
KBA identifies users by asking them to answer specific security questions in order to verify their identity for account opening, login, or other online activities. The promise of KBA is, unfortunately, met by some harsh realities. That's why organizations are looking for alternatives.
"The promises of knowledge-based authentication have given way to some harsher realities."
Forbes Technology Council
KBA was thought to be effective because only the individual knows all the details needed to verify their own identity.
KBA often relies on the same personal information exposed in most data breaches.
High-profile data breaches regularly make headlines, which means KBA data is regularly exposed and openly sold on the dark web.
"Knowledge-based authentication, based on questions derived from PII, is no longer reliable."
BankInfoSecurity.com
KBA was supposed to be secure because it emphasized answers to personal questions only the individual would know.
Information used to craft KBA questions can also often be found online — a quick social media search can reveal the name of your pet or the name of your oldest nephew.
"16 percent of security questions had answers routinely listed publicly in online social networking profiles."
Secrets, Lies, and Account Recovery, Google Survey
KBA was accepted by regulators as a secure method of identity authentication for AML/KYC compliance.
Regulators are now increasingly calling for stronger, more robust methods of authentication.
The National Institute of Standards and Technology (NIST) no longer endorses security questions and answers as a secure authentication method.
KBA was considered a secure authentication method because it relies on information only the user would purportedly know and remember.
20 percent of users forget the answers to their security questions within six months. This creates the need for re-verification and results in user frustration.
"Businesses must assume that fraudsters have the exact same knowledge of personal information as their customers." PINDROP

There is a better way to verify online identity.

Learn how to choose the right solution with The Identity Verification Solution Buyer's Guide.
KBA Alternatives for Online Identity Verification
If you've already decided KBA is not right for you, you have some options to consider. Below we've summarized a handful of alternatives:

Two-Factor Authentication (2FA)
Two-factor authentication requires more than one method of identity verification. It combines any two of: something the user knows, something they have or something they are. Most commonly, 2FA combines a username/password with a unique verification code that is texted or emailed to the user.
Pros
SMS-based 2FA is effective for password resets and suspicious logins because of the near-ubiquitous penetration of smartphones, it's a convenient method for users.
Cons
SMS-based 2FA is vulnerable to key logging, SMS-spoofing, man-in-the-middle and man-in-the-browser attacks. Despite it being considered among the most user-friendly methods, NIST has declared SMS-based 2FA insecure.
Credit Bureau-Based Solutions
Many online identity verification systems call out to one of the big three credit bureaus, Experian, Equifax and TransUnion, who then search for an identity match within their vast repositories of consumer credit data.

Pros
These are authoritative databases with a wealth of identifying information. They are easy to tap into via API and can provide a fast, low cost, unintrusive customer experience.
Cons
There are simply too many weaknesses to rely on this method as the single source of identity verification. People with little or no credit history often cannot be matched, common names can result in a false positive and it allows for limited geographic coverage. Importantly, these solutions fail to verify that the user providing the information is the same user behind the transaction.

Database Solutions
When used for identity verification, database solutions often leverage online, social media and offline data (and sometimes behavioral patterns) to detect if an online user is authentic, a fraudster or a bot.
Pros
A positive aspect of database solutions is that they can pull from a variety of sources to verify a person's identity markers. This can reduce the number of manual identity checks a business has to perform. They also tend to be API-based which leads to a flexible, customizable solution.
Cons
Database solutions fail to verify that the user providing the information is the same user behind the transaction. They also lack a degree of authority since they don't rely on government-issued IDs. These solutions also often fail to meet many compliance/regulatory requirements.
Online Identity Verification Solutions
Online identity verification solutions use a mix of artificial intelligence, computer vision and verification experts to determine if a government-issued ID is authentic and belongs to the user. Some solutions also perform identity validity checks via a corroborating selfie to ensure that the person holding the ID is the same person shown in the ID photo, and even liveness checks to assure the person holding the ID is physically present during the transaction.
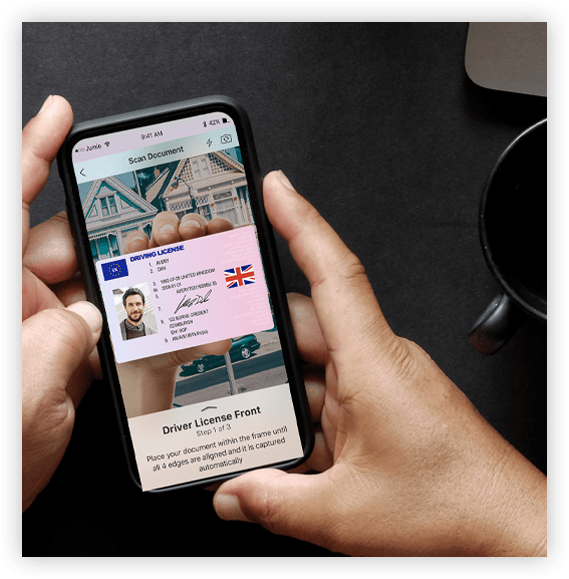
Pros
Solutions use a variety of AI, biometrics, machine learning and human review to verify the user's identity. The solutions tend to deliver a high level of verification assurance and results are generated in near-real-time.
Cons
Since the solutions require users to capture a photo of their ID and take a selfie, there is some friction introduced to the verification process.
Get Started
Let a Jumio expert show you how easy it can be to integrate our automated identity verification and AML solutions into your existing processes.
Black Ddesert Knowledge Base Authentication Keys
Source: https://www.jumio.com/kba-alternatives/